Why Your eCommerce Website Needs Stronger Security Measures

In today’s digital landscape, eCommerce websites are prime targets for cybercriminals. This article breaks down essential eCommerce security practices every business should implement to stay safe online.
Hence, a solid eCommerce security strategy is crucial for a growing eCommerce company.
In this article, we take a look at the most common security threats, based on the OWASP Top 10, that affect eCommerce brands today, and the best practices you should implement to protect your eCommerce site and your customers.
Key takeaways
- Security Threats: eCommerce sites face risks such as Cross-Site Scripting (XSS), SQL injection, Distributed Denial of Service (DDoS) attacks, malware, hacker fraud, and phishing, all of which target sensitive customer information and site functionality.
- 4 Pillars of Security: Privacy, integrity, authentication, and non-repudiation are the foundational principles for ensuring secure online transactions and protecting customer data.
- Best Practices: To secure your eCommerce site, implement practices such as investing in secure platforms, tracking transactions, updating software regularly, enforcing strong passwords, and using SSL encryption.
- Open Source Risks: Open-source eCommerce platforms can be vulnerable to cyber-attacks unless regularly maintained with updates and security patches, often requiring dedicated developers or SaaS solutions for robust protection.
On this page:
What is eCommerce security?
eCommerce security focuses on maintaining safe and secure electronic transactions for the buying and selling of goods and services over the web. Several protocols are put in place to ensure the safety and protection of those involved in the online transaction.
Consumers need to know that they can trust your brand before they can shop with you. Having robust eCommerce security practices in place is crucial to building trust with your customers. Besides the financial consequences, a cyber-attack or breach can significantly harm your online store’s reputation. Customers will be reluctant to continue shopping at an online store that has put their confidential information at risk.
6 most common eCommerce security threats you need to be aware of
Details such as bank accounts, credit/debit card details, passports, and driving licenses are regularly submitted online. Many hackers try to access this information and sell it on the dark web, which in turn can be used for identity theft. Here, we share some of the most common threats facing eCommerce websites large and small.

1. Cross-Site Scripting (XSS)
Cross-site scripting is a widespread cyber attack strategy. XSS involves an attacker inserting a malicious piece of coding, usually in Javascript, onto a web page of your eCommerce site. When the browser sees this coding, it sees it as a regular script and executes it. This script can access an end-user’s session cookie information so attackers can impersonate them. This enables the hacker to access confidential information and exposes the victim’s computer to malware installations and phishing attempts.
While this type of attack doesn’t necessarily harm your eCommerce site, it primarily targets your customers, which can put a dent in your consumer relations. In 2016, for example, a single XSS attack affected over 6,000 eCommerce sites and resulted in stolen customer credit card information.
2. SQL injection
A SQL injection can affect any site or web-based application that utilizes a SQL database. Magento is one notable eCommerce platform that uses a SQL database to store customer information. With a SQL injection, the hacker can insert a malicious SQL query inside a packaged payload, which will look like legitimate SQL. On processing the SQL query, however, the attacker will gain access to the database to either view the sensitive information, delete entries, or create an administrator account for themselves so that they can gain full access to the eCommerce system via the backend.
3. Distributed Denial of Service (DDoS)
A DDoS takes down your eCommerce site by overwhelming your server with requests that come from hundreds, even thousands, of IP addresses. These IP addresses have usually been compromised by malware and forced into making several requests to a website. This type of attack overloads your servers, resulting in slow performance or even taking your site offline temporarily, which prevents your consumers from making any purchases. Since DDoS attacks come from many sources, they are a challenge to stop. With more devices coming online, DDoS attacks will likely continue to grow in strength and prevalence.
High-profile sites are primarily susceptible to these attacks, but smaller websites could be vulnerable if their web hosting provider or DNS provider has been compromised. In October 2016, DNS provider Dyn became a victim to a DDoS attack, affecting thousands of websites that were forced offline.
4. Hacker fraud
Hackers attempt many methods to steal user credential information from eCommerce websites. With the use of automation, bots can test username and password data to find successful combinations using brute force.
If a hacker finds that an eCommerce website has security issues, they will use this to their advantage in an attempt to steal the website’s database of user credentials. The hacker will then use this stolen data to try users' credentials on other sites so they can identify people who use the same username and password combination in multiple places.
There are some malicious bots out there that are designed to hack into an account. Some bots can quickly go through a dictionary or word list in a matter of seconds to try and gain access to an unsuspecting user's account.
More specifically, a hacker who hacks into accounts or steals card information from your server is attacking your eCommerce company with a double-edged sword. Here’s what we mean by that:
If a hacker makes purchases via a stolen account, your company will lose the trust of the affected customer, as well as the goods that were mistakenly sent to the hacker. Moreover, the affected customers would need to be refunded. So, you lose out in terms of trust as well as capital.
5. Malware
Malware is software that's intended to cause harm to a website, server, or network. The malicious software can take the form of viruses, trojans, worms, or any other such forms. Malware can do a wide range of harmful activities from controlling computers and forming a botnet as a part of a more extensive DDoS attack to steal sensitive information or perform spam activities.
6. Phishing
Phishing scams often come in the form of an email that has been disguised to look like it's coming from someone that you know, or from a reputable company. These emails usually contain a link that either seeks to steal information, or installs malware on a device to gain access to personal information and credit card details.
Here's how you could spot a phishing attempt:
- Mismatched URLs: The URL in the email or message doesn’t match the anchor text, or the URL contains out-of-place words, letters, or numbers.
- Poor spelling and grammar: The email or message that you receive contains obvious spelling and grammatical errors that would be unbefitting of a large company to send out.
- You didn’t initiate the correspondence: If you receive an “urgent message”, “final warning”, or “lucky winner” message, ask yourself if you’re even expecting any such messages before handing over any information.
- The offer/threat is too good/bad to be true: If the message is offering a large sum of money or a lofty prize, or worse yet, a hefty fine or legal action, take a step back and ensure the message is legitimate.
The (hidden) problem with open source eCommerce platforms
Open source software accounts for a large chunk of eCommerce platforms. Figures from AheadWorks show that 29.1% of eCommerce sites operate on Magento, and 26.5% on WooCommerce.
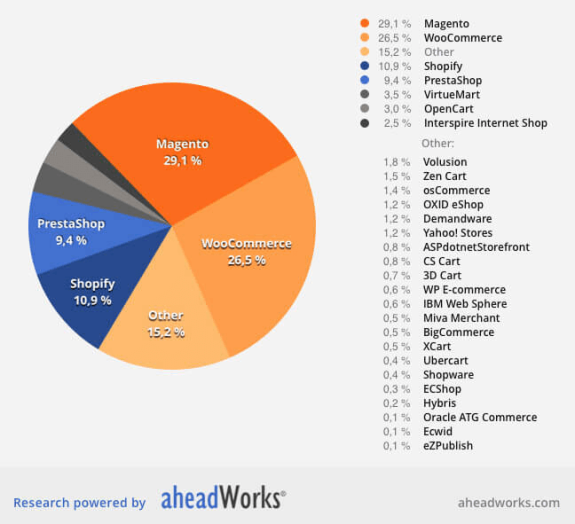
(29.1% of eCommerce sites operate on Magento, and 26.5% on WooCommerce)
The primary benefit of open source eCommerce platforms is that they’re free to download, install, and use. The downside is that there is a lot of onus on you to make sure your eCommerce site runs properly. You need to hire a team of developers to look after your eCommerce site such as installing upgrades and security patches, running normal maintenance processes, and migrating to the latest version of the software.
Failure to do any of these activities promptly will make your eCommerce site vulnerable to many of the cyber-attacks that we’ve listed above. We’ve seen hundreds of cases of eCommerce brands using open source software that become victims of cyber-attacks. For example, in 2016, one malware attack targeted over 6,500 Magento sites.
If you can’t afford to hire developers, you’ll be spending a large amount of your time maintaining your site, and less time growing your business. SaaS-based, or propriety, eCommerce platforms can reduce your total cost of ownership in terms of customization, updates, hosting, and replatforming. According to Forrester, 80% of on-premise open source spending goes towards maintenance. With a SaaS-based solution, all the nitty-gritty aspect of maintaining and updating the eCommerce platform is taken care of by the software provider.
The 4 pillars of eCommerce security
Before we delve into the best practices of eCommerce security, let us familiarize ourselves with the four pillars that every eCommerce brand must follow.
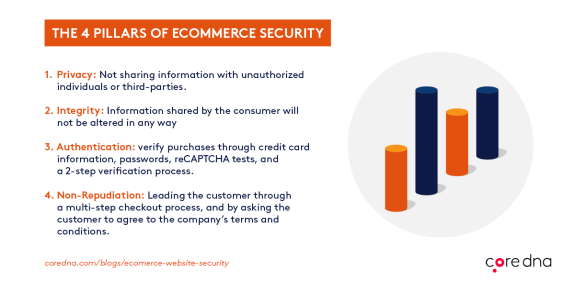
1. Privacy
In the world of eCommerce, privacy means not sharing information with unauthorized individuals or third-parties. When a consumer shop online, both their personal and financial details should only be accessible to you, and no one else. If this information is disclosed to anyone for any reason, it's a breach of confidentiality.
Since the introduction of EU data privacy regulation GDPR back in May 2018, a number of similar legislation has been introduced in the US and across the world. California, for example, in the California Consumer Privacy Act (CCPA) in June 2018. This legislation has encouraged many eCommerce brands to obtain user consent before processing cookie data and personal information. A handful of companies have received fines for failure to comply with these regulations such as an Austrian retail entrepreneur who was fined 4,800 euros (approx. $5,300) for using CCTV that recorded public sidewalk.
2. Integrity
Besides privacy, eCommerce brands must demonstrate integrity when handling data. Integrity means information shared by the consumer will not be altered in any way. The idea behind this pillar is to ensure business only use data that customers have given to a site. Any signs of data tampering will damage consumer confidence.
The best way to show integrity is to have a clearly written and easily accessible data privacy and cookie policy that outlines how you intend to handle and store your consumer’s data. You can make this policy document available on the consumer consent form. Below is a screenshot of UK retailer Tesco’s user consent form. Notice how accessible the privacy and cookies policy is.
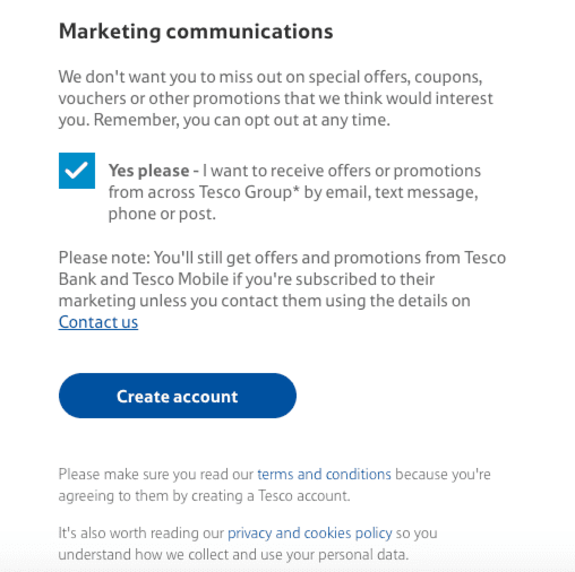
(Tesco has a clear privacy and cookies policy | Source)
3. Authentication
For any online transactions to take place, both the seller and buyer must be truthful in identifying who they are.
There are many ways an online retailer can authenticate who they are selling to. While the future of authentication involves machine learning and fingerprint scanning, today’s eCommerce sites can verify purchases through credit card information, passwords, reCAPTCHA tests, and a 2-step verification process involving two of the user’s previously configured devices.
4. Non-Repudiation
Non-repudiation means that there is no room for either party to deny their actions or commitments. This entails that a contract is signed or agreed to, and that a series of actions were taken (and logged) to indicate that both parties are entering purposefully and consciously entering into an agreement.
The principle behind non-repudiation provides another layer of security that confirms that the information exchanged between buyer and seller has been received, and the purchase will go ahead as planned.
In an eCommerce context, this is done by leading the customer through a multi-step checkout process, and by asking the customer to agree to the company’s terms and conditions. This shows that the seller offered products in exchange for accepting agreements and transferring money, and it also shows that the buyer willingly complied.
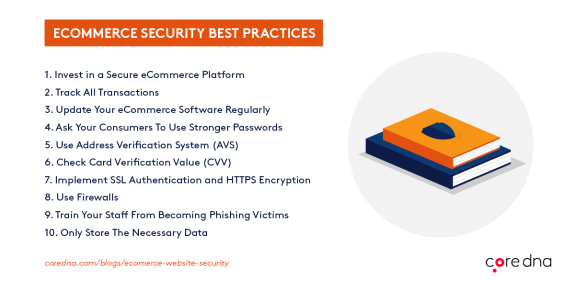
Getting started: 10 eCommerce website security best practices
The following are action items and best practices you can put in place to comply with the four pillars of eCommerce security.
1. Invest in a secure eCommerce platform
When deciding on an eCommerce platform, take the time to review the company's security track record. As mentioned, open source eCommerce platforms may be popular, but they are prone to cyber attacks if they’re not properly maintained. SaaS eCommerce platforms, like Core dna, are secure solutions that are looked after by a dedicated team who conduct regular audits to iron out any flaws.
2. Track all transactions
Take the time to audit your transactions. You should have your finance team analyze transactions to ensure the billing and shipping addresses are the same (or at least in the same country). If they don’t match, then it is often considered a warning sign of fraudulent activity. The physical location of the customer provides a strong indication of whether the transaction is legitimate. Some eCommerce solutions offer IP address tracking to enable online sellers to block transactions from countries which are deemed high risk.
3. Update your eCommerce software regularly
It's crucial for eCommerce brands that are using open source solutions, in particular, to update regularly. Make sure you keep on top of any updates, bug fixes, and security patches and install them promptly. If you’re on an open source platform, make sure you use enterprise or business-grade antivirus and anti-malware to protect your site and customers.
4. Ask your consumers to use stronger passwords
Hackers can use algorithms and bots to guess consumer passwords. For simple passwords, it wouldn’t take long for these malicious procedures to go through all the possible password combinations to find the right one. A commonly used password such as ‘1234567’ or ‘password’, as identified by SplashData, should be avoided at all costs!
Instead, encourage your customers to set longer passwords that contain at least one capital letter, one special character, and a number. You can also impose stricter password protocols to ensure your customers set stronger passwords.
5. Use AVS
Address Verification System (AVS) compares the billing address the customer provided with the address the credit card provider has on their systems. Most payment gateways offer this feature, and it's a simple but useful way to verify transactions further.
6. Check CVV
The Card Verification Value (CVV) is the 3 or 4 digit number that is found on the reverse of a credit or debit card. Under PCI (Payment Card Industry) standards, retailers can’t store this CVV number for future transactions, but they can keep hold of names, addresses, and payment card details.
Verifying the CVV makes it difficult for cybercriminals who have the credit card number but not the actual physical card since the most payment gateways block transaction from going through when the CVV doesn’t match the card details. So, while you may not be able to keep CVV numbers on file, you can ensure CVV protection by using a trusted payment gateway like PayPal or Stripe.
7. Implement SSL authentication and HTTPS encryption
Utilizing SSL (Secure Sockets Layer) and HTTPS encryption helps to authenticate the identity of your business and gives consumers the added reassurance that your eCommerce site is safe. You can go one step better and integrate a stronger EV SSL (Extended Validation Secure Sockets Layer). Here’s what these terms mean:
- SSL Security: SSL (Secure Sockets Layer) provides a secure channel between two machines or devices operating over the internet or an internal network. It encrypts the communication between those two machines, keeping it safe from third-party snooping and attacks. A website with SSL security is easy to spot; Their website URL will contain ‘https://’, rather than just ‘https://’. The additional ‘S’ stands for ‘secure’. You can purchase an SSL certificate from any reputable domain name seller.
- Extended Validation Secure Sockets Layer: Extended Validation SSL Certificates are a new form of SSL Certificate. They intend to give customers an added sense of security, as the legal name of the company is shown in the address bar when their website is visited. This assures visitors that they’re not looking at a dummy or malicious website.
Consumers can spot the absence of the SSL and HTTPS encryption when they see a red cross against your URL, and ensuring this doesn't appear demonstrates a higher level of trustworthiness to your end user.
8. Use firewalls
Firewalls act as the first line of defense against cyber-attacks, preventing attackers from breaching your network and gaining access to sensitive information.
A basic firewall will ensure that only proper types of traffic such as organic, paid, social media, and referral traffic will be allowed to reach your website. These firewalls manually block specific IPs that you can also detect attacks from, but this is a manual process which requires expertise to perform.
Thankfully, a new breed of firewall, known as Web Application Firewalls (WAF) devices has emerged. A WAF can inspect, in detail, all traffic to and from your website. They can identify and actively prevent a multitude of cyber-attacks, from SQL injections to XSS. These firewalls come equipped with databases of known offenders, letting you rest easy knowing that these malicious IPs are not able to interact with your website at all. Many providers sell this as a service coupled with Content Distribution Network (CDN) or DDOS-prevention functionality. Core dna comes with WAF as standard.
9. Train your staff
To prevent your employees from becoming victims of phishing scams and other threats, organize training sessions to make them aware of the risks. Here are some things to discuss with your team:
- Phishing scams: Teach your staff how to spot phishing emails and messages.
- Malware checks: Think about investing in malware software and training your staff on how to run weekly scans to check for malicious software.
- How to report suspicious behavior/software: It’s important to document and explain the protocols around reporting suspicious software, behavior, or messages.
- GDPR regulation: If you’re dealing with EU-based customers, your employees must be knowledgeable and ensuring the company’s compliance with the GDPR.
...And here are some ways to have those discussions and training sessions:
- Live stream training sessions: You could live stream your security training sessions across your company’s offices by live streaming from your head office.
- Host training videos within your intranet: Record and keep your security training videos within your intranet so employees can access it, comment on it, and share it quickly and easily.
- Gamify security training: Use a learning management system to house and deliver your training courses, and make use of the platforms gamification features to have a leaderboard as well as a reward system for employees who complete the courses.
- Outsource your security training: Not sure your internal team is savvy enough to lead training sessions? Draft in professionals to deliver the training instead (just make sure you record it!)
10. Only store the necessary data
It’s quite an old habit to retain past transactions from previous years. But actually, there is no real reason to keep hold of thousands of customer records, particularly when it contains credit card details, expiry dates, and other personal information. It’s best to regularly purge old records from your database and keep just enough data for handling refunds and chargebacks.
Establish ironclad eCommerce security, and consumer trust will follow
As more software systems become connected by the day, the threat of breaches and cyber-attacks have become an increasing concern. As an eCommerce company, you should follow the four pillars of privacy, integrity, authentication, and non-repudiation.
You can shore up the security of your eCommerce site by following these best practices:
- Invest in a secure platform
- Track all transactions
- Update software regularly
- Ensure consumers user strong passwords
- Use the Address Verification System (AVS)
- Check Card Verification Values (CVVs)
- Implement SSL Authentication and HTTPS Encryption
- Install firewalls
- Train your staff on basic security procedures
- Purge old data
However, if you decide to opt for an eCommerce SaaS platform, the bulk of the work regarding security patches, updates and maintenance are taken care of by the provider, leaving you with more time to spend on growing your eCommerce brand and keeping your customers happy.













