Website Security: What You Need to Know Before It's Too Late
Website security is not something to put on the back burner—it’s a top priority for any business. This article explores what you need to know about website security to protect your site from growing threats.
The biggest threat facing the modern internet is the number of websites running outdated code - millions of websites have been left wide open to hackers, as a result.
In this post, our very own in-house (white-hat) hacker, runs you through the exact methods hackers use to compromise sites and breaks down the safety measures you can enact to protect yourself.
Key takeaways
- Outdated software is a major risk: Millions of websites run outdated code, making them easy targets for hackers. Regular patching is crucial.
- Open-source CMS platforms attract hackers: Both white-hat (ethical) and black-hat (malicious) hackers exploit vulnerabilities in open-source platforms like WordPress.
- Look out for red flags: Insecure websites often show signs like missing HTTPS, pop-ups, security warnings, and lack of contact or privacy info.
- Proactive security measures matter: Use SSL certificates, firewalls, managed platforms, and regular server scans to stay ahead of threats.
On this page:
Why hackers LOVE open source CMS
The source code for open-source software is available (under license) for anyone to use, which has plenty of advantages when compared to proprietary alternatives. It’s inexpensive (if not free), there’s ample support available through thriving online communities, it’s transparent, it’s reliable (because so many people are keeping an eye on it,) and there’s no lock-in.
Open-source software gives you the power of the crowd. But, the crowd is made up of both good and bad actors. Inspecting the source code of open-source CMSs for security defects has become big business, and the leading players in this industry can be split into two groups:
1. ‘White Hat’ hackers
White-hat hackers are paid handsomely for preventing damaging security exploits (a security exploit is just another term for a security vulnerability.) They do so by finding and secretly reporting exploits to software creators. WordPress offers a “Bug Bounty” of thousands of dollars to those who report significant security bugs, which has helped turn the color of many a hacker’s hat from black to white.
Once reported, software creators develop a solution to the exploit, consulting with the hacker to make sure it can’t be worked around. If the solution’s successful, an update to the software is released, and the public’s notified that their system needs to be updated immediately.
But, despite these steps taken by white-hat hackers to keep the public safe, a large proportion of open-source software users don’t actually apply the updates, which means their systems can easily be compromised.
2. ‘Black-Hat’ hackers
Black-hat hackers sell the exploits they find on the black market, rather than reporting them to software creators. With millions of websites built on open-source platforms such as WordPress (which powers more than 30% of the web) these exploits are like gold dust in the wrong hands.
One of the favored techniques of black-hat hackers everywhere is called “Google hacking.” When Google crawls websites, it unintentionally, but unavoidably, indexes the identity and version of every site’s CMS. Hackers then use this information to create vast lists of sites running outdated CMS versions, along with their specific vulnerabilities (there are currently 5,000 entries in the Google Hacking Database.)
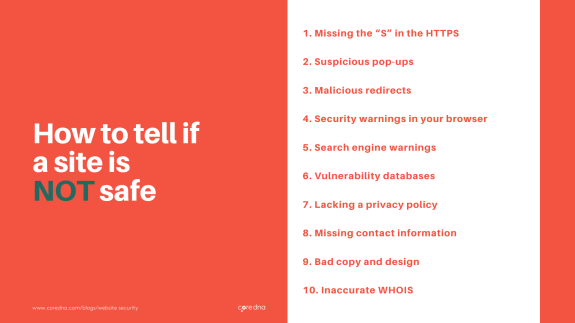
How to tell if a site is NOT safe: 10 signs to look for
(How to check website security)
1. Missing the “S” in the HTTPS
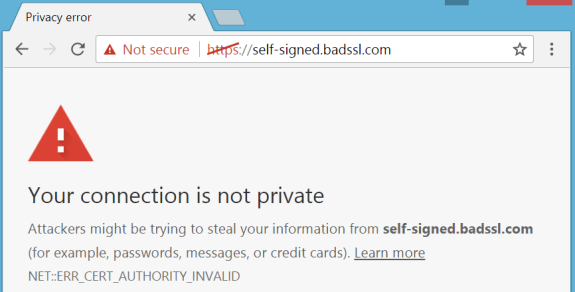
The “S” in HTTPS stands for “Security.” If your website URL starts with just “HTTP,” and there’s no lock icon next to the URL in the address bar, then your site’s not secure.
2. Suspicious pop-ups
Pop-ups advertising third-party products or software installations are a definite no-no.
3. Malicious redirects
Automatic redirects should ring alarm bells. Respectable companies want their visitors to have a streamlined, intuitive user experience. Websites that offer the opposite should raise suspicion.
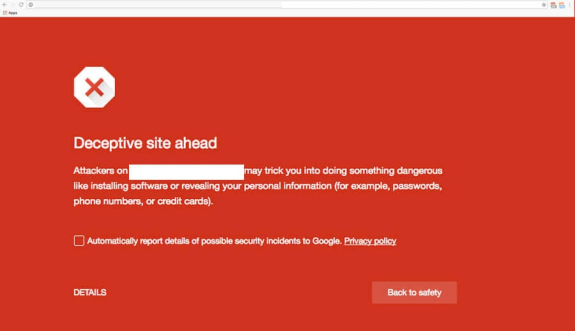
4. Security warnings in your browser
Chrome will issue a warning in response to security concerns like if a site contains malware, or a page is trying to load scripts from an unauthenticated source.
5. Search engine warnings
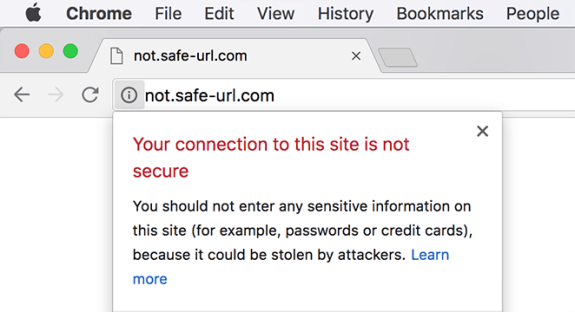
Google displays warnings like "This site may harm your computer" or "This site may be hacked" if they deem your site unsafe.
6. Vulnerability databases
Vulnerability databases, such as IBM’s ISS X-Force database, collect, maintain, and publish lists of security vulnerabilities that could be affecting your site.
7. Lacking a privacy policy
A website’s privacy policy clearly communicates how data is collected, used, and protected. It’s a legal requirement in many countries and a sign that a site’s owner cares about your security.
8. Missing contact information
A website that’s safe to use will likely have some means of communication listed, even if it’s only an email address or a web form.
9. Bad copy and design
Legitimate companies put a lot of effort into branding, design, and copy on their sites. Spelling errors, gibberish text, poor image quality, broken links, and on-site spam should all raise suspicions.
10. Inaccurate WHOIS
WHOIS is a protocol that enables you to find the names and contact details of a domain’s owners. It’s not perfect: it’s easy for owners to provide false information, but it’s a good enough way to triangulate other methods.
How we secure our clients’ websites (and how you can do the same)
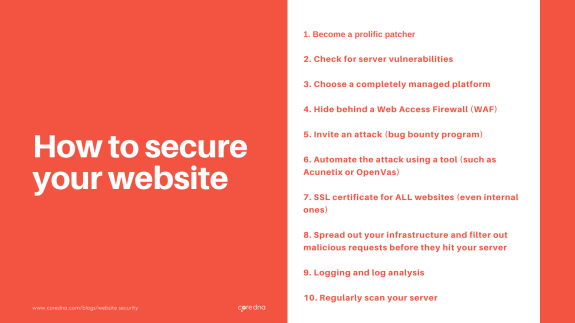
1. Become a prolific patcher
The best and easiest way to maintain website security is to stay alert to all the new patches that are released for your CMS, applying them as soon as they’re made available, which makes all the hard work put in by white-hat hackers worthwhile.
Take a look at your CMS now - if you’re not using the latest security patch version, then there will already be exploits out there waiting to cause you harm. If you’re technically-minded, you can look up your CMS’s version in one of the vulnerability databases to see precisely what you’re up against.
2. Check for server vulnerabilities
Your CMS platform is the most likely source of your website’s vulnerabilities, but it’s by no means the only one. The web server running your site also needs to be patched and maintained. Unlike updating your CMS, however, this can be a rather involved procedure, requiring downtime if you only have one server running your site.
3. Choose a completely managed platform
There is, of course, a comprehensively secure solution to this problem, and that’s to choose a completely managed platform.
At Core dna, our security team is certified OSCP (Offensive Security Certified Professional) and responsible for ensuring the security of our clients’ websites in several ways:
- Because Core dna is a unified platform, it doesn’t require any updates from the customer’s end. At all. Ever.
- As soon as an update for our platform or any software is released, our team of update-addicts rolls it out across our entire platform, permanently eliminating any vulnerabilities.
- Our platform was constructed with redundancy in mind so that components can be updated without downtime.
- Core dna is a closed-source platform, and as such, its source code is not subject to public scrutiny. The less information out there, the harder it is for hackers to cause damage.
4. Hide behind a Web Access Firewall (WAF)
The Core dna platform is secured by a Web Access Firewall, or WAF for short. A WAF inspects all of the traffic heading towards a site, filtering out any malicious activity or attempted attacks before they ever arrive.
These firewalls are fantastic for security and pretty affordable if you shop around. Still, you need to have your WAF solution implemented by a professional, because incorrect implementations are easily bypassed.
5. Invite an attack (have a bug bounty program)
The ultimate test of a website’s security is to have somebody attack it. We’re talking about the practice of “penetration testing,” and there are many security businesses that provide this service (yet another example of hackers using their skills for good instead of evil.)
The only problem is that the cost of having a trained pro go over your website with a fine-toothed comb is prohibitively expensive for many companies.
Fortunately, Core dna has its very own hacking expert who performs penetration testing regularly. We also have the platform tested by independent third parties frequently, to make sure we can stand up against our peers.
6. Automate the attack
While there’s no substitute for a real-life hacker testing your website’s security, there are automated tools, widely available online, that can do the job for you, albeit to a lesser degree.
A word of warning though, these tools should only ever be used by a professional or on a testing environment, because if the tool ends up being successful in exploiting your site, you’ll suffer an outage as a result!
Sidenote: There are a number of automated test suites for penetration testing, a quick Google search reveals a vast sea of options.
These all work on a fairly consistent principle whereby they are configured with a wide suite of exploit strategies that they execute one and a time until they have run through their entire stable. In this way, they essentially test via brute force and exploring all options in an automated fashion.
A couple of tools that you might want to use: Acunetix (paid) and OpenVas (free)
7. SSL certificate for ALL websites (even internal ones)
Make sure you have your site set up with an SSL certificate, and it’s running over HTTPS.
An SSL certificate ensures that your website is encrypted as it travels over the internet so that if it’s intercepted along the way, user details, passwords, and even credit card details will be distorted and indecipherable to hackers. All websites on the Core dna platform are set up with an SSL certificate.
Not only will an SSL make your site more secure, but you’ll also be missing out on traffic if you haven’t got one installed: Chrome (and most other web browsers) will warn visitors to your site, and Google may penalize your search ranking if you don’t have one.
8. Spread out your infrastructure and filter out malicious requests before they hit your server
A Denial of Service (DoS) attack is an attempt to render your website unavailable by flooding it with more requests than your server can handle. While a DoS attack emanates from a single source, a Distributed Denial of Service (DDoS) attack comes from multiple sources simultaneously and is therefore much harder to contend with.
DDoS attacks are frequent, and you have to take steps to mitigate them. You won’t have any of your precious data stolen, but your website will go down.
Some sites have known DOS vulnerabilities (listed online) that render them utterly defenceless to hackers. With such vulnerabilities, a straightforward DoS attack can topple even the most hardened hosting infrastructure, and the only solution is to update your patches immediately.
The best CDN providers offer their clients a degree of protection against DoS and DDoS attacks by having gigantic infrastructures capable of withstanding enormous volumes of traffic.
They also provide the ability to analyze and filter out malicious requests before they hit. You’ll still experience slower user performance, which is frustrating when it starts affecting bounce rates. Still, it beats having your site crash for days at a time.
9. Logging and log analysis
Websites with poor security get hacked all the time (sad, but true), and the first thing to get stolen is their user databases.
These databases contain all the usernames and matched passwords of a site’s account holders, and because people use the same logins wherever they go on the web (despite plenty of advice to the contrary), hackers can use the stolen logins to break into other sites.
Taking the safety measures listed in this article will prevent hackers from capturing your database and encrypt passwords in the unlikely event that they are stolen. But, logging and log analysis are also crucial elements in the security process.
Through careful monitoring, you can identify any user from a single IP address who attempts multiple logins with different usernames and passwords, shutting down their activity before it’s too late.
The more you log, the better you’ll understand the behavior patterns of customers (and staff!) and the quicker you can respond to anything suspicious.
10. Regularly scan your server
A piece of malicious code uploaded to your site can have disastrous consequences. Of course, you want to try and stop this happening by strictly controlling what can be submitted to any area of your website, but hackers will always find a way.
For example, a malicious user can leave a harmful piece of code in a comment on your blog, which can then cause significant damage to a subsequent user who views it. When the comment loads, that harmful code can trigger anything from a pop-up window opening to a malicious redirect, a stolen session or password, and even the complete compromising of a computer.
It’s, therefore, good practice to regularly scan your server for trojans, malware, and other malicious files using a tool like Lynis, which is, essentially, anti-virus software for your server. It will find and remove any problematic code before it can cause any significant problems.
So, in summary: Security is not static
The field of cybersecurity is constantly evolving. With black-hat hackers working ‘round the clock to come up with new and ingenious ways to break into websites, only white-hat hackers have the skills and insider-knowledge required to find open-doors and close them before nefarious characters pass through.
If you use the Core dna platform, you'll have your very own white-hat hacker on your side. If not, then following all the steps outlined above will go a long way towards keeping you safe.













